Archetype
10.10.10.27
Recon
Basic scan
Starting with a basic scan using nmap we see what ports are open.

ports found
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
1433/tcp open ms-sql-s
In depth scan
We then do a more in depth scan on the ports listed to see what services is being used on them. We use nmap -sCV -p135,139,445,1433 10.10.10.27 to get the results in the image below.

Vuln Scan on ports found
Next we do a script scan on the above ports. Using nmap --script=vuln -p135,139,445,1433 10.10.10.27 we get the results in the image below.
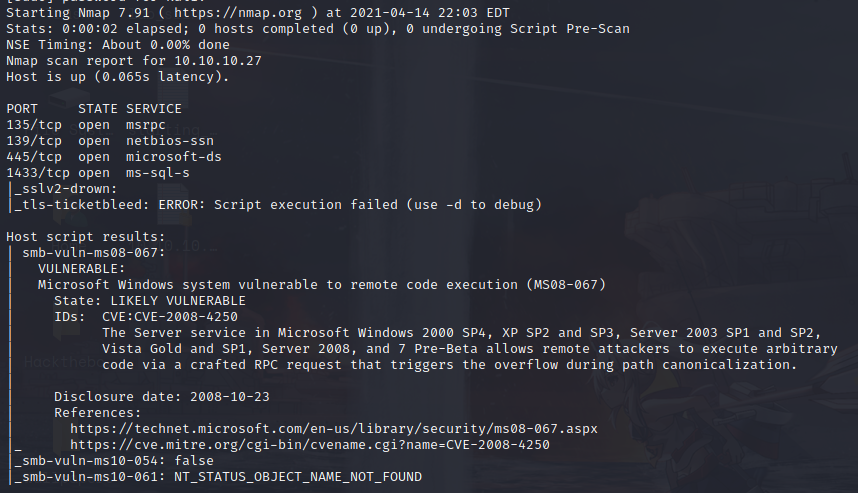
CVEs found
CVE-2008-4250: Microsoft Windows system vulnerable to remote code execution (MS08-067)
what we found
port 135 is a microsoft remote protocol. It is used to provide access to microsoft services and applications over the network more info
Port 139 is utilized by NetBIOS Session service. Enabling NetBIOS services provide access to shared resources like files and printers not only to your network computers but also to anyone across the internet.
Port 445 is the microsoft directory services, it is used by SMB (server message block). SMB is a network protocol used , mainly in Windows networks for sharing resouces (ie printers and files) over a network
Port 1433 is a relational database managment system. As a database server, it is a software product with the primary function of storing and retrieving data as requested by other software applications which may run either on the same computer or on another computer across a network (including the Internet)
smbclient
Using nmap we can see the avialable shares are if anonymous access is avialable.
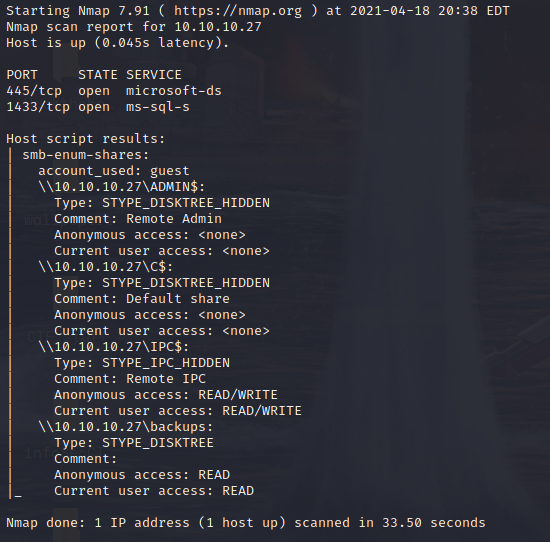
Using smbclient we test connectivity to a Windows share. It can be used to transfer files, or look up a share name. Since the backups share allows anonymous access we will try that one.
Using smbclient -N \\\\10.10.10.27\\backups we can connect the to the backups share

We are able to succsefully connect. Using ls we can see what is in this share. We find a prod.dtsConfig file, using the get command we can retrieve this file to our host system.
A DTSCONFIG file is an XML configuration file used to apply property values to SQL Server Integration Services (SSIS) packages. The file contains one or more package configurations that consist of metadata such as the server name, database names, and other connection properties to configure SSIS packages.
prod.dtsConfig file content
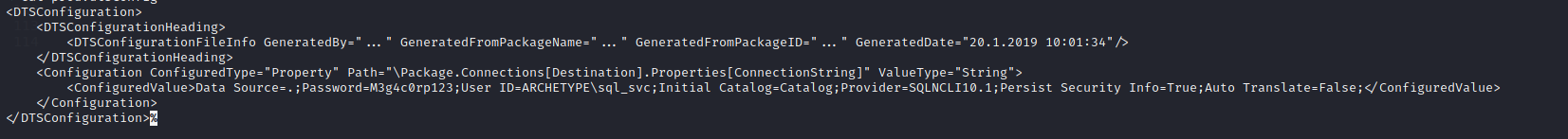
It has a ID: ARCHETYPE\sql_svc and a password: M3g4c0rp123 . Using impackets mssqlclient.py script we can connect the sql server using the its id and password.
We enter python3 mmssqlclient.py ARCHETYPE/sql_svc@10.10.10.27 -windows-auth. This allows us to connect to sql server. we
Last updated