Arctic
Nmap Scan
From the nmap scan we see 3 ports open

2 ports have Windows RPC Services and 1 port has file message transfer protocol (fmtp). After searching for some exploits for these services and I didn't find anything...
So next I tried to go to 10.10.10.11:8500 in firefox and it showed a filesystem.

So next I looked through the files and found a login page for adobe ColdFusion version 8.

And this gave me the information needed to gain access to the machine.
Exploit
I found an exploit in msfconsole relating to this product pretty quickly but I am trying to avoid using the Metasploit framework. So I resorted to the next best thing, looking for an exploit in GitHub, and found a small python script.
Using this script I can perform an Arbitrary File Upload exploit and upload a reverse shell payload.

Here we can see the payload in the /userfiles/file directory
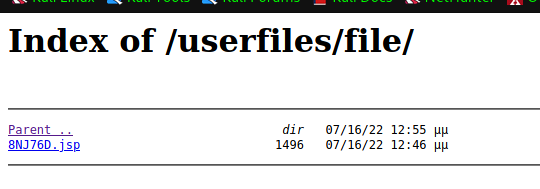
And by clicking the JSP file we can catch a reverse shell on the machine.

And from here I can grab the user flag :D
Privilege Escalation
First I examined the systeminfo to see what I'm working with.

So we are in a Windows Server 2008 R2 Standard with an OS version of 6.1.7600 N/A Build 7600.
I wanted to try and upload a winPeas exe to see if I can find any other points of interest so I downloaded the exe and checked the PowerShell version on the machine using powershell.exe (Get-Host).Version so I can see what commands I can use to download the file from my python http server. Sadly the exe didn't work so the next best thing was windows exploit suggester.
Using the systeminfo output and this python script I can get possible exploits.

From the output, we see some kernel exploits and after some experimenting and testing I narrowed down that MS10-059 that allows us to perform privileged escalation.
So using PowerShell I can transfer the exe to the target machine.


The next step was to set a listener and run that exe and...pray

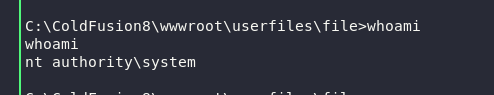
And success!!! :)
We are now the superuser.
Last updated