Soccer
nmap scan results
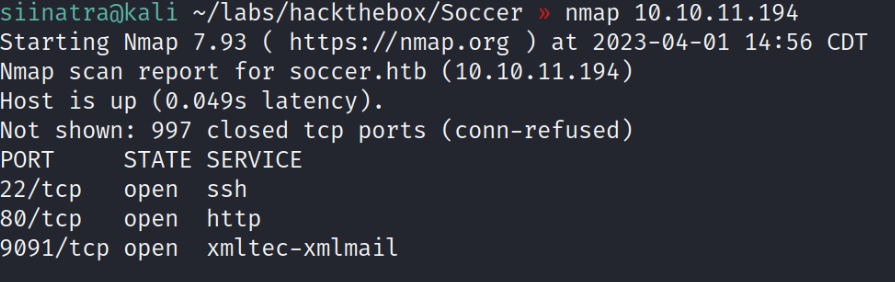
From the scan we see that port 22,80,9091 are open, no clue what service is running on port 9091 so lets start with port 80.
But first we need to update the /etc/hosts file so we can view the website using the following command sudo echo "10.10.11.194 soccer.htb" >> /etc/hosts
soccer.htb
When we visit soccer.htb we see some website/blog about soccer.

When we inspect the websites code, not much can be found that will help us so next best thing is the check for any web directories. Using dirbuster we see that there is a directory called tiny.
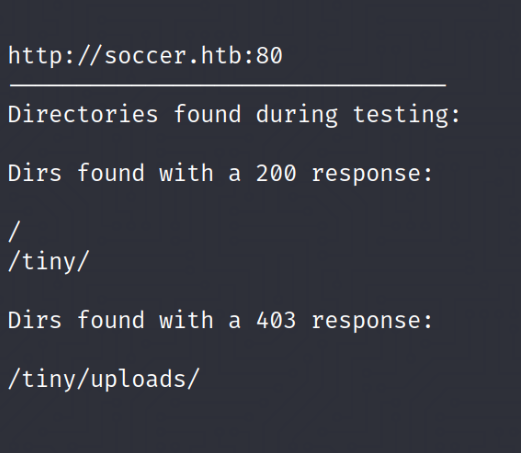
Tiny File Manager
When we visit this directory we see a login page
And after some I found the github repo for this project and it lists the default login credentials

And it worked we now have access to the application

From here we can upload a php reverse shell.
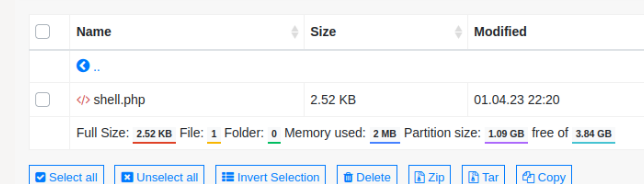
And we got a shell but we are logged in as www-data so we can't really get the user flag

After looking around and trying some basic priv sec methods I didn't find much but there was a subdomain listed in the /etc/hosts file.

soc-player.soccer.htb
So after adding the subdomain to out hosts file we can now view the new subdomain.

And we can see some options we can select some options, if we select sign up we can make an account for whatever this is. Once I made an account, and a pop up appears giving is our ticket id.

If we look at the webpages code we can see a script block that used to send data to a websocket, which explains our mystery service running on port 9091.
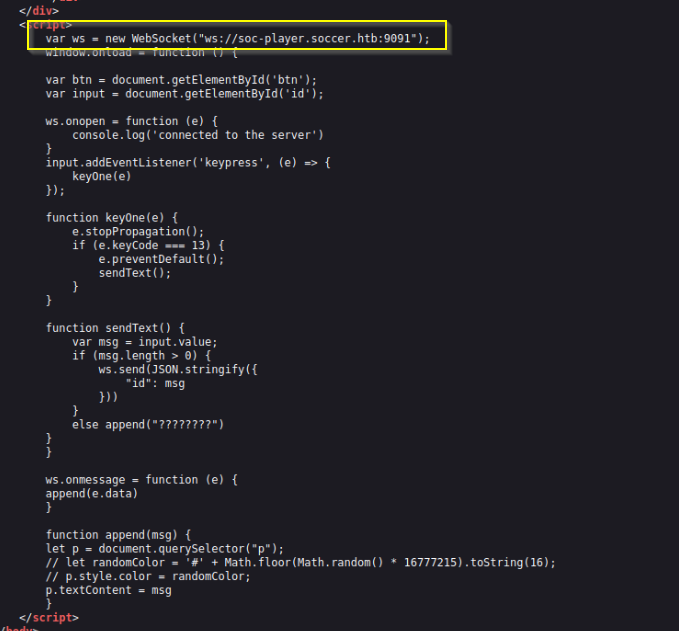
After ALOT of googling on what can I do with this, I found a blog post about Automating Blind SQL Injection with a script that can be edited for us to use.
So I followed the steps in the blog post and edited the python script. I ran it and and used sqlmap -u "http://localhost:8081/?id=1" -p "id" --exclude-sysdbs to send the payload and after sometime and troubleshooting I was able to list the database and its tables including a username and password

User & Root
Using the username and password we found we can just ssh into the target player and get the user flag

Next I use linpeas to find any privilege escalation points, and if found that the user player can execute dstat as root
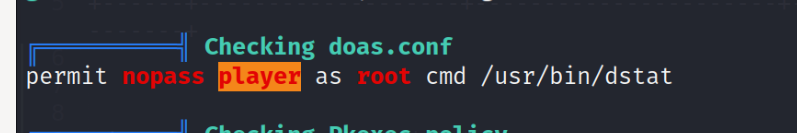
Knowing this we can just go gtfobins and find how to escalate to root.
