Bucket Digital Forenics

Scenario
Welcome, Defender! As an incident responder, we're granting you access to the AWS account called "Security" as an IAM user. This account contains a copy of the logs during the time period of the incident and has the ability to assume the "Security" role in the target account so you can look around to spot the misconfigurations that allowed for this attack to happen.
Question 1
What is the full AWS CLI command used to configure credentials?
Answer: aws configure
aws cli configure documentation
Question 2
What is the 'creation' date of the bucket 'flaws2-logs'?
Answer: 2018-11-19 20:54:31 UTC
Why?
Using the the following command the wil set the region to us east and list buckets in s3. aws configure set region "us-east-1" && aws s3api list-buckets, below is the output that was given from the command.

Question 3
What is the name of the first generated event -according to time?
Answer: AssumeRole

Why?
Because this is the earliest time recorded.
Question 4
What source IP address generated the event dated 2018-11-28 at 23:03:20 UTC?
Answer: 34.234.236.212
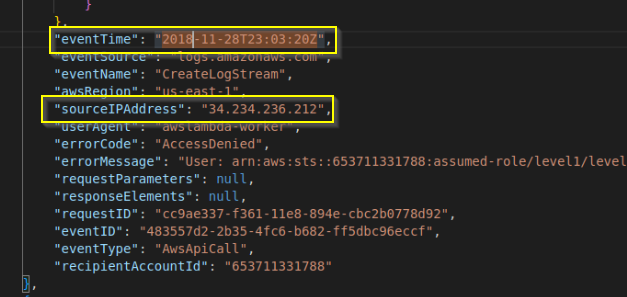
Why? Using the find feature in vscode I just searched for the time that was given and
Question 5
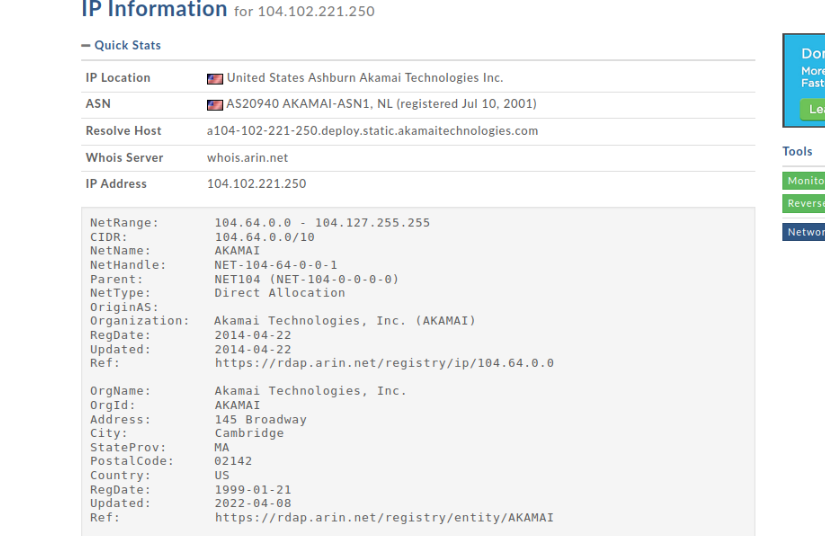
Which IP address does not belong to Amazon AWS infrastructure?
Answer: 104.102.221.250
Why? Using whoisdomaintools we can search up this up and we see that it is not assigned to AWS
Question 6
Which user issued the 'ListBuckets' request?
Answer: level3

Why? If we search for the event named ListBuckets we can find the username tag with the user associated with that event
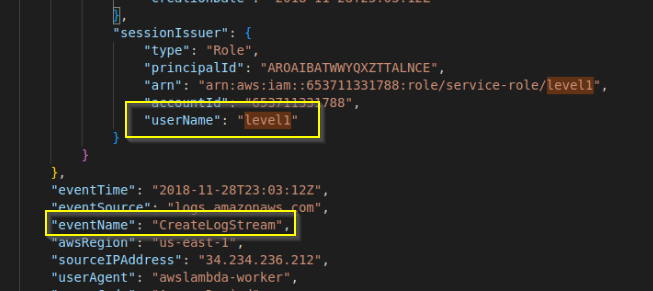
Question 7
What was the first request issued by the user 'level1'?
Answer: CreateLogStream
Why? If we search for level1 username and compare the times of the events we see that CreateLogStream was the earliest time.
This was my first Blue Team challenge, thanks for reading and expect more to come.
Last updated